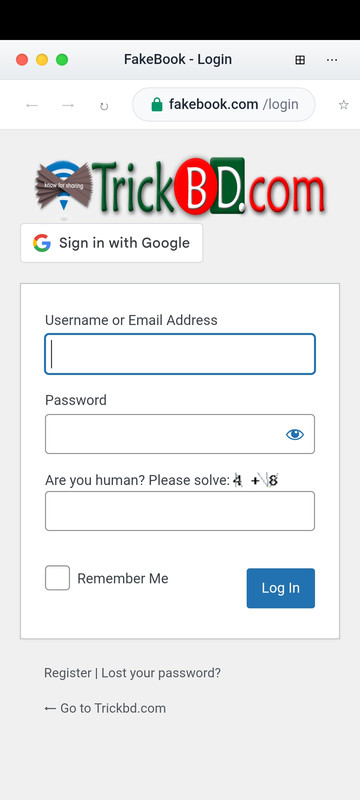
This educational project demonstrates how Browser-in-the-Browser (BITB) attacks work, where hackers use fake browser windows (via iframes) to trick users into entering login credentials.
Always verify URLs, enable 2FA, and avoid entering credentials in pop-up windows. Also, ensure your website is protected from being embedded in an iframe.
Websites can prevent their content from being embedded in iframes by using HTTP headers like X-Frame-Options or Content-Security-Policy (CSP). This prevents attackers from creating fake login pages inside iframes on malicious sites.
-
X-Frame-Options: Use this header with
DENYorSAMEORIGINvalues to block your site from being embedded in iframes.DENY: The website cannot be embedded in any iframe.SAMEORIGIN: The website can only be embedded in iframes from the same origin (same domain).
-
Content-Security-Policy (CSP): This provides more granular control over which domains can embed your site, helping protect against BITB attacks.
Many large companies, such as Google, Facebook, and Twitter, block their sites from being embedded in iframes to prevent phishing and other types of attacks.
🌐 Free Hosting & Subdomain
📸 How does this look?
🎥 Educational Demo
⚠️ Warning: This project is for educational purposes only. Never use it for malicious activities. Always obtain explicit consent before conducting a ny security tests.