(https://github.com/denizariyan/VSterilizer/actions/workflows/codeql-analysis.yml)
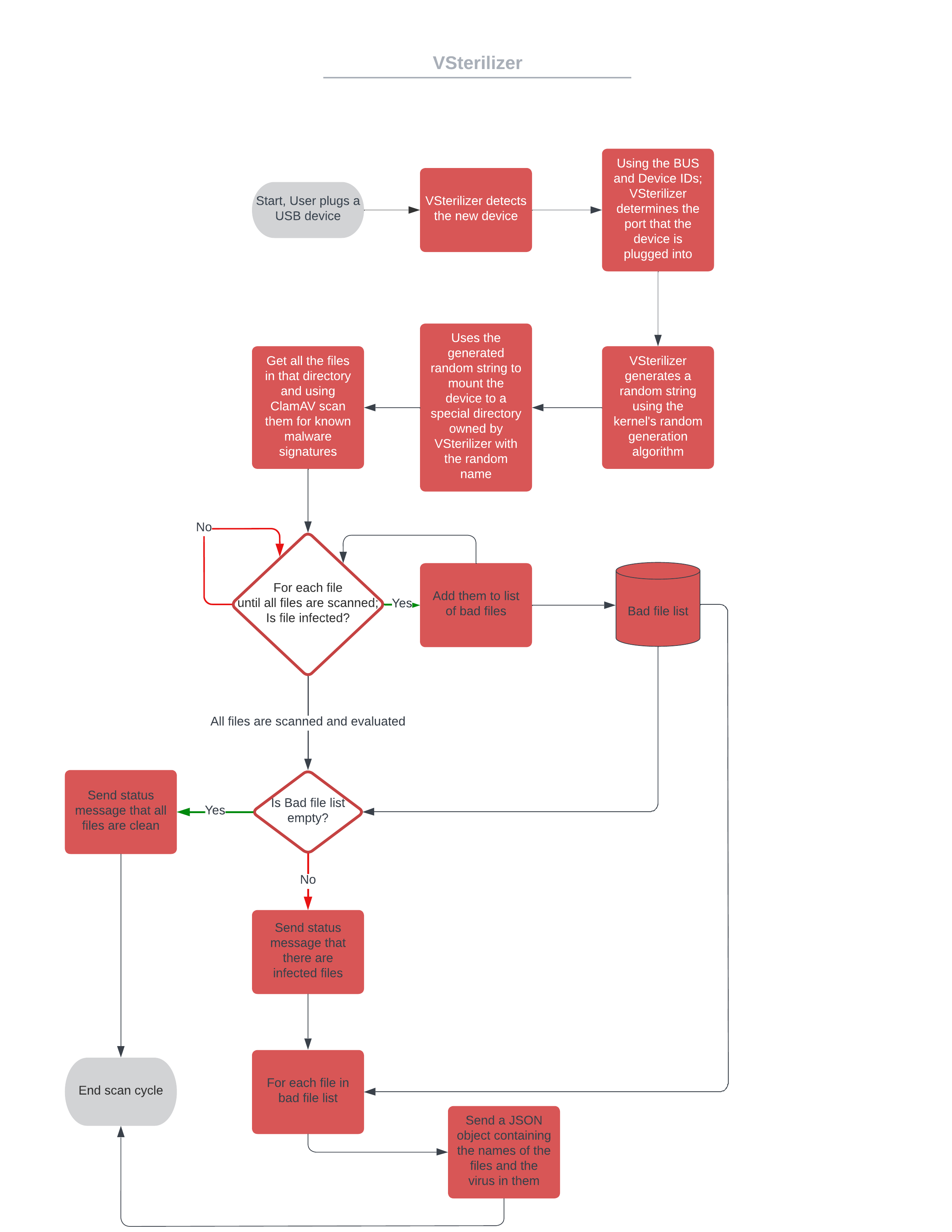
VSterilizer is a USB scanning service that scans any USB device plugged into the computer that is running the scanner utility and reports the results through API endpoints.
This installation steps assume that you are running Fedora 35. There could be slight changes to the shell commands if you are running another distro but the steps in general will be the same.
sudo dnf install nodejsgit clone https://github.com/denizariyan/VSterilizer.gitnpm installsudo dnf install clamav clamd clamav-updatesudo node main.js2. After running the script you will get a response similar to the one below mentioning that both the the scanner utility and the API listener utility is running
Started to monitor for USB inserts!
Listening on port 8080!4. The script will detect the newly plugged in USB device and start scanning it immediately and send a status message to the API endpoint that it is accessing a new USB device. Example API call below
{
args: {},
data: '{"status":"Accessing the USB Device..."}',
files: {},
form: {},
headers: {
Accept: 'application/json, text/plain, */*',
'Content-Length': '40',
'Content-Type': 'application/json',
Host: 'httpbin.org',
'User-Agent': 'axios/0.26.1',
'X-Amzn-Trace-Id': 'Root=1-626fcfec-21c50ae55f9e79a838a867aa'
},
json: { status: 'Accessing the USB Device...' },
origin: '<SENDER_IP_ADDRESS>',
url: 'http://httpbin.org/post'
}{
args: {},
data: '{"status":"Scan completed, no infected files has been detected."}',
files: {},
form: {},
headers: {
Accept: 'application/json, text/plain, */*',
'Content-Length': '65',
'Content-Type': 'application/json',
Host: 'httpbin.org',
'User-Agent': 'axios/0.26.1',
'X-Amzn-Trace-Id': 'Root=1-626fcff2-39b0b20222be8fd42873f046'
},
json: { status: 'Scan completed, no infected files has been detected.' },
origin: '<SENDER_IP_ADDRESS>',
url: 'http://httpbin.org/post'
}First a status message that mentions that the USB device is infected will be sent.
{
args: {},
data: '{"status":"Scan completed, check infected file list!"}',
files: {},
form: {},
headers: {
Accept: 'application/json, text/plain, */*',
'Content-Length': '54',
'Content-Type': 'application/json',
Host: 'httpbin.org',
'User-Agent': 'axios/0.26.1',
'X-Amzn-Trace-Id': 'Root=1-626fd172-2951bf061e93fc434ad08ce5'
},
json: { status: 'Scan completed, check infected file list!' },
origin: '<SENDER_IP_ADDRESS>',
url: 'http://httpbin.org/post'
}After that a result message that includes the details of the infected file(s) will be sent.
{
args: {},
data: '{"badFile":"eicar.com","virus":"Win.Test.EICAR_HDB-1"}',
files: {},
form: {},
headers: {
Accept: 'application/json, text/plain, */*',
'Content-Length': '54',
'Content-Type': 'application/json',
Host: 'httpbin.org',
'User-Agent': 'axios/0.26.1',
'X-Amzn-Trace-Id': 'Root=1-626fd172-2de80c305bd1bb492dd73e42'
},
json: { badFile: 'eicar.com', virus: 'Win.Test.EICAR_HDB-1' },
origin: '<SENDER_IP_ADDRESS>',
url: 'http://httpbin.org/post'
}This will run all automated tests and report back the results.
npm testExample test result
$ npm test
> [email protected] test /home/deari/projects/VSterilizer
> jest --silent=true
PASS tests/config.test.js
PASS tests/scan.test.js
Test Suites: 2 passed, 2 total
Tests: 5 passed, 5 total
Snapshots: 0 total
Time: 0.928 s, estimated 1 sPull requests are welcome. For major changes, please open an issue first to discuss what you would like to change.
Please make sure to update tests as appropriate.