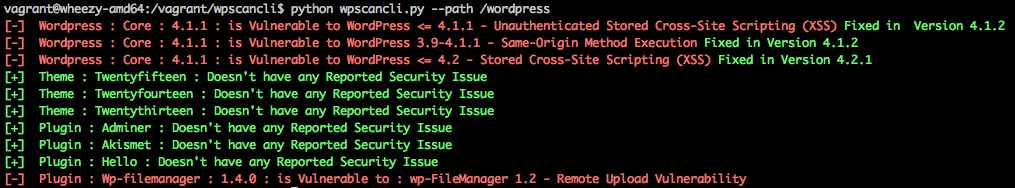
A commandline vulnerability reporter using WP-CLI and WPVulnDB
Specially useful for server admin's managing the wordpress backend and what a quick list of vulnerable plugin's. Running wpscan is a tiresome process and does non needed bruteforce. Being a server admin the list of plugin's / themes could be directly extracted.
usage: wpscancli.py [-h] --path PATH [--vulnonly]
This program is used to run a quick wordpress scan via wpscan api. This
command depends on wp-cli
optional arguments:
-h, --help show this help message and exit
--path PATH Provide URL
--vulnonly Only List vulnerable Items
Credit (C) Anant Shrivastava http://anantshri.info
Wordpress management part is handed over to WP-CLI as it is doing its job too well. The list of plugin/theme's and respective versions is obtained from wp-cli are then used to extract results from wpvulndb.
- export report in csv/xml/json format
- WP-CLI is used to get information from wordpress instance
- WPVulnDB API used to get the vulnerability data.
On 5th July 2017 We have renamed the project from wpvulndb_commandline to wpvulndb_cmd.