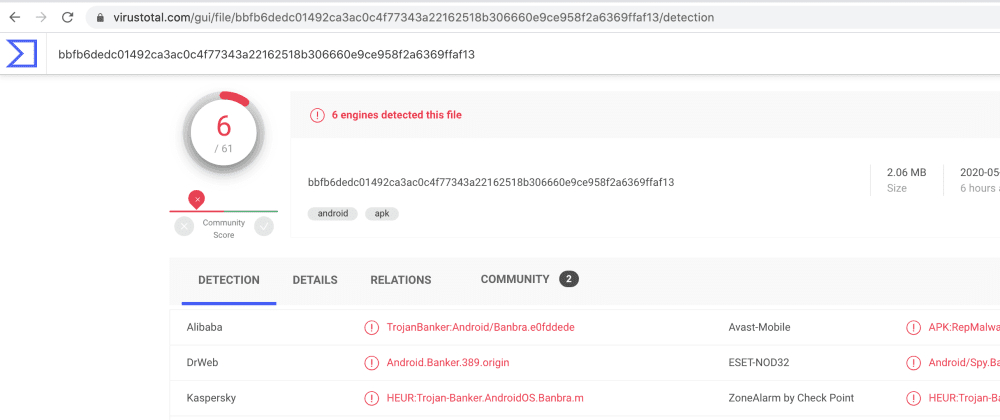
Read about 'Serverless' data security and its ugly truth.
Read about 'Serverless' data security and its ugly truth.
 A gaming PC can be a pricey investment. Even more reason to guard it with the best antivirus. Here are the 3 best antivrus software for Gaming PCs in 2021.
A gaming PC can be a pricey investment. Even more reason to guard it with the best antivirus. Here are the 3 best antivrus software for Gaming PCs in 2021.
 Reverse engineering a NodeJS Discord malware and exposing the authors by finding the webhook they used.
Reverse engineering a NodeJS Discord malware and exposing the authors by finding the webhook they used.
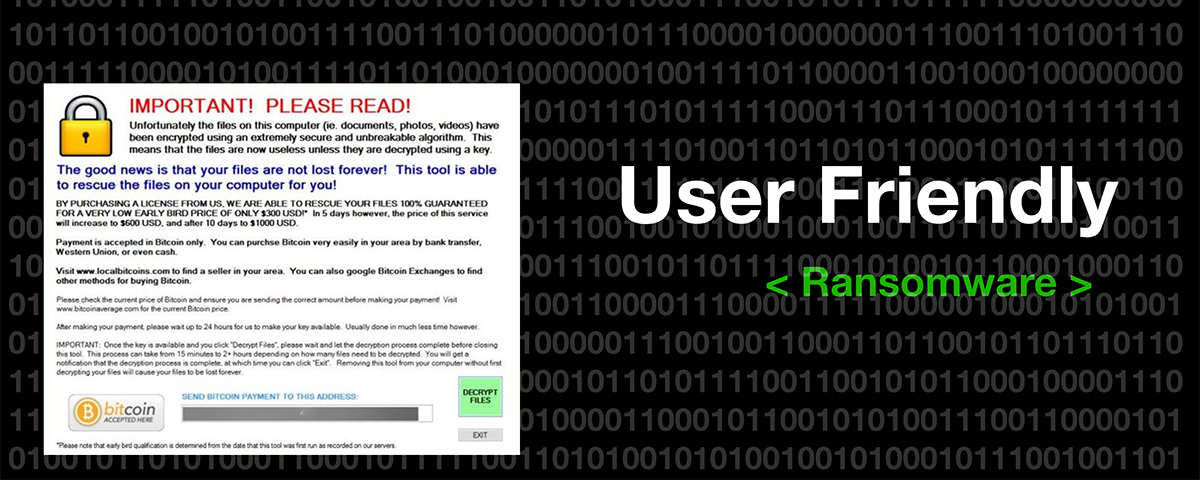
 What is ransomware? Why is it so dangerous? Who can be affected? How to get rid of it…or maybe to prevent it?
What is ransomware? Why is it so dangerous? Who can be affected? How to get rid of it…or maybe to prevent it?
 There are several reports of threats and attacks on crypto wallets every day. You must be on the lookout to keep your investment safe and secure from hackers.
There are several reports of threats and attacks on crypto wallets every day. You must be on the lookout to keep your investment safe and secure from hackers.
 In this article, you will learn about the signs of ransomware and how you can identify them.
In this article, you will learn about the signs of ransomware and how you can identify them.
 Emotet, which was once a Banking Trojan and became a full-blown botnet was the most successful and prevalent malware of 2020 by a long way.
Emotet, which was once a Banking Trojan and became a full-blown botnet was the most successful and prevalent malware of 2020 by a long way.
 An ad redirecting users to browser hijacking software was recently spotted on CNN's election tracking site. Ahead of election season, it's reason for concern
An ad redirecting users to browser hijacking software was recently spotted on CNN's election tracking site. Ahead of election season, it's reason for concern
 Machine learning is famous for its ability to analyze large data sets and identify patterns. It is basically a subset of artificial intelligence. Machine learning uses algorithms that leverages previous data-sets and statistical analysis to make assumptions and pass on judgments about behavior.
The best part, software or computers powered by machine learning algorithms can perform functions that they have not been programmed to perform.
Machine learning is famous for its ability to analyze large data sets and identify patterns. It is basically a subset of artificial intelligence. Machine learning uses algorithms that leverages previous data-sets and statistical analysis to make assumptions and pass on judgments about behavior.
The best part, software or computers powered by machine learning algorithms can perform functions that they have not been programmed to perform.
 With increased hacking activity focused on vulnerable businesses and at-home employees, cybersecurity has become a major business priority.
With increased hacking activity focused on vulnerable businesses and at-home employees, cybersecurity has become a major business priority.
 Make an inexpensive BadUSB from an old USB drive and learn about Windows shortcut files and how malicious actors are using .lnk files to spread malware.
Make an inexpensive BadUSB from an old USB drive and learn about Windows shortcut files and how malicious actors are using .lnk files to spread malware.
 A glimpse over Command and Control attacks and frameworks, how they happen, and how they can affect our daily lives.
A glimpse over Command and Control attacks and frameworks, how they happen, and how they can affect our daily lives.
 Jailbreak Checkrain Checkra1n Security Scam Malware
Jailbreak Checkrain Checkra1n Security Scam Malware
 Ransomware is a sort of malware that cybercriminals use to extort cash. It holds information to ransom with encryption or by keeping users out of their devices.
Ransomware is a sort of malware that cybercriminals use to extort cash. It holds information to ransom with encryption or by keeping users out of their devices.
 Apple started making computers in 1976, long before they became common in most households in the developed world.
Apple started making computers in 1976, long before they became common in most households in the developed world.
 A walkthrough the different types of malware - from viruses to botnets, ransomware and phishing. Learn more and get protected!
A walkthrough the different types of malware - from viruses to botnets, ransomware and phishing. Learn more and get protected!
 Following my last article about a Discord malware, we now take a deeper look inside the inner workings of the PirateStealer malware.
Following my last article about a Discord malware, we now take a deeper look inside the inner workings of the PirateStealer malware.
 Cyber-warfare and espionage have long been common weapons in the arsenal of governments, armies, and intelligence agencies around the world.
Cyber-warfare and espionage have long been common weapons in the arsenal of governments, armies, and intelligence agencies around the world.
 Knowing how to prevent malware attacks or mitigate those that are already on your devices is crucial. Here are seven effective tips you need to adopt to secure
Knowing how to prevent malware attacks or mitigate those that are already on your devices is crucial. Here are seven effective tips you need to adopt to secure
 This article addresses the current issue of digital security and proposes solutions to particular threats that a business owner might face in the near future.
This article addresses the current issue of digital security and proposes solutions to particular threats that a business owner might face in the near future.
 Common misconceptions about hacking that makes you vulnerable and how to avoid them.
Common misconceptions about hacking that makes you vulnerable and how to avoid them.
 PlugX & PortScan Chinese Malware Surfacing in Non-tech Companies - shows Motivation Was Financial.
PlugX & PortScan Chinese Malware Surfacing in Non-tech Companies - shows Motivation Was Financial.
 An article about how each Cross-Site Scripting Attack behaves in order to understand how to defend our systems on the web against them
An article about how each Cross-Site Scripting Attack behaves in order to understand how to defend our systems on the web against them
 Jackware is a form of malware designed purely to cause chaos and destruction. Here's how it works.
Jackware is a form of malware designed purely to cause chaos and destruction. Here's how it works.
 Even though malicious Python packages are found every day by our security researchers, a new type of malware we call RAT mutants is catching our attention.
Even though malicious Python packages are found every day by our security researchers, a new type of malware we call RAT mutants is catching our attention.
 SolarWinds, a leading provider of IT monitoring and management solutions for enterprises, disclosed that it had fallen prey to a widespread supply chain attack
SolarWinds, a leading provider of IT monitoring and management solutions for enterprises, disclosed that it had fallen prey to a widespread supply chain attack
 When a USB outlet or charger cable already attached to an adapter is modified to supply power and gather data, this is known as juice jacking.
When a USB outlet or charger cable already attached to an adapter is modified to supply power and gather data, this is known as juice jacking.
 Cybersecurity risk regarding ransomware and how it is evolving with cryptocurrency.
Cybersecurity risk regarding ransomware and how it is evolving with cryptocurrency.
 Scam advertisements across major media outlets originate from DoubleClick and Xandr/AppNexus
Scam advertisements across major media outlets originate from DoubleClick and Xandr/AppNexus
 The Colonial Pipeline Breach has shown us that ransomware attacks are not going away anytime soon and having been increasing due to the COVID-19 pandemic.
The Colonial Pipeline Breach has shown us that ransomware attacks are not going away anytime soon and having been increasing due to the COVID-19 pandemic.
 Blockchain has not only become the fundamental technology for cryptocurrencies; it has also become a reliable means of detecting malware quickly and accurately.
Blockchain has not only become the fundamental technology for cryptocurrencies; it has also become a reliable means of detecting malware quickly and accurately.
 Conservative estimates put company’s monthly income at a minimum $500,000.
Conservative estimates put company’s monthly income at a minimum $500,000.
 David Mahdi gives advice on how identity-first security helps prevent no-click malware attacks from succeeding.
David Mahdi gives advice on how identity-first security helps prevent no-click malware attacks from succeeding.
 Being steps ahead of cyber attackers matters a lot to companies. As good as this sounds, the required mechanism to deal with the cyber menace appreciates costs.
Being steps ahead of cyber attackers matters a lot to companies. As good as this sounds, the required mechanism to deal with the cyber menace appreciates costs.
 ReThink Cybersecurity - Cyber Wellness the New Healthly Livign Trend
ReThink Cybersecurity - Cyber Wellness the New Healthly Livign Trend
 Enterprise administrators and individuals must defend their computer resources from numerous attacks to avoid a data breach
Enterprise administrators and individuals must defend their computer resources from numerous attacks to avoid a data breach
 The protection of your computer is becoming very important as more and more hackers learn how to make smarter invasions that would not be noticed at first.
The protection of your computer is becoming very important as more and more hackers learn how to make smarter invasions that would not be noticed at first.
 Glupteba is a blockchain-backed trojan that uses a P2P network.
Glupteba is a blockchain-backed trojan that uses a P2P network.
 With Cybersecurity constantly evolving, each month has its own malware that poses the greatest threat. These are the malware threats that were most concerning.
With Cybersecurity constantly evolving, each month has its own malware that poses the greatest threat. These are the malware threats that were most concerning.
 The Uyghurs, an ethnic minority in China have been targeted by fake human rights documents and websites intended to take advantage of their persecution in China
The Uyghurs, an ethnic minority in China have been targeted by fake human rights documents and websites intended to take advantage of their persecution in China
 Image steganography is a technique that attackers use to hide a secret piece of text, malware, or code inside of an image. This technique is difficult to detect
Image steganography is a technique that attackers use to hide a secret piece of text, malware, or code inside of an image. This technique is difficult to detect
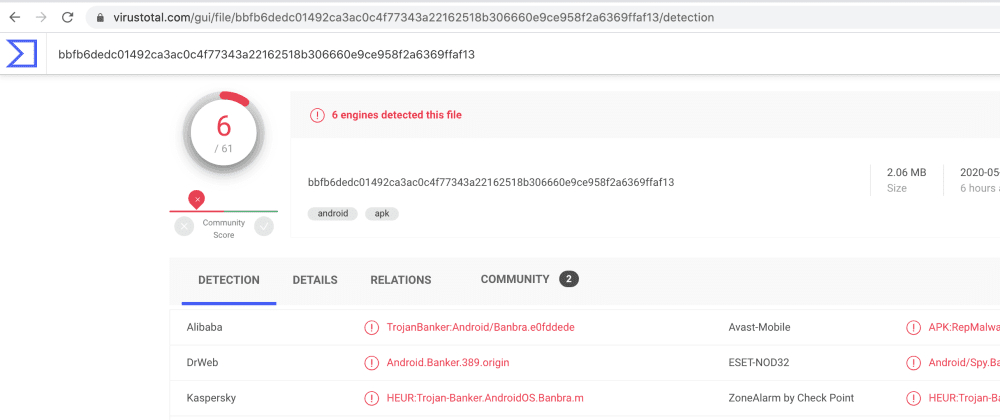 Android malware apps are nothing new, but this one is of particular interest in how it implements no such functionality that can be readily detected by security products. The apps named DEFENSOR ID and Defensor Digital rely mainly on Android's Accessibility Service to conduct malicious activities, and go undetected.
Android malware apps are nothing new, but this one is of particular interest in how it implements no such functionality that can be readily detected by security products. The apps named DEFENSOR ID and Defensor Digital rely mainly on Android's Accessibility Service to conduct malicious activities, and go undetected.
 Malware is everywhere these days. You've probably been a victim at some stage, and you may well not even know it. From all-too-visible ransomware attacks to botnets and adware, it's a complex picture, and new variants are emerging all the time.
Malware is everywhere these days. You've probably been a victim at some stage, and you may well not even know it. From all-too-visible ransomware attacks to botnets and adware, it's a complex picture, and new variants are emerging all the time.
 These are the top 10 Antivirus software options on the market in 2021. Depending on your device (Mac, PC, Android, or iOS), there is an appropriate Antivirus.
These are the top 10 Antivirus software options on the market in 2021. Depending on your device (Mac, PC, Android, or iOS), there is an appropriate Antivirus.
 We all use email on a regular basis, but we aren’t always cognizant of the email security standards we use. If a hacker gains access to your account, or manages to fool you into downloading an attachment with malware via email, it could have devastating consequences for your business.
We all use email on a regular basis, but we aren’t always cognizant of the email security standards we use. If a hacker gains access to your account, or manages to fool you into downloading an attachment with malware via email, it could have devastating consequences for your business.
 Introduction:
Introduction:
 Malicious software (Malware) are either programs or files that are intended to cause harm to a system and thereby its user.
Malicious software (Malware) are either programs or files that are intended to cause harm to a system and thereby its user.
 Are you also frustrated by getting fake messages and want to identify that fake message? Then must move down for more detail about fake messages.
Are you also frustrated by getting fake messages and want to identify that fake message? Then must move down for more detail about fake messages.
 Android Malware has started spreading by creating auto-replies to messages in WhatsApp. It's hidden cleverly in dubious apps that are surprisingly good.
Android Malware has started spreading by creating auto-replies to messages in WhatsApp. It's hidden cleverly in dubious apps that are surprisingly good.
 Most experienced gamers realize that many different kinds of malware can slow down their games.
Most experienced gamers realize that many different kinds of malware can slow down their games.
 All you need to know about the security loopholes in your android device and how to protect your mobile phones from privacy invasions and security breaches.
All you need to know about the security loopholes in your android device and how to protect your mobile phones from privacy invasions and security breaches.
 Let's look at some of the most significant risks posed by your personal digital devices, and what we can do to boost your security.
Let's look at some of the most significant risks posed by your personal digital devices, and what we can do to boost your security.
 This isn’t a review, and — as much as I wish it was — it’s not a promotion either. It’s a firsthand account… a testament to the continual negative impact of frauds in the crypto space. I wrote this article to make the community aware that LocalBitcoins doesn’t consider to accept moral responsibility when users get scammed on the platform.
This isn’t a review, and — as much as I wish it was — it’s not a promotion either. It’s a firsthand account… a testament to the continual negative impact of frauds in the crypto space. I wrote this article to make the community aware that LocalBitcoins doesn’t consider to accept moral responsibility when users get scammed on the platform.
 Malware protection should act the same way, as a set of shields that protect the entire browser from any type of malware, not just traditional threats.
Malware protection should act the same way, as a set of shields that protect the entire browser from any type of malware, not just traditional threats.

Even if you aren't very tech-savvy, you may have heard about vulnerabilities in both Android and iOS platforms making the news. Despite these headlines, smartphone hacking is a real challenge many of us still don't take seriously.
 How to prepare yourself to face the Cybersecurity Threats in the year ahead? Check out the top 5 of the most expected attacks in 2021.
How to prepare yourself to face the Cybersecurity Threats in the year ahead? Check out the top 5 of the most expected attacks in 2021.
 Check Point Research encountered several attacks that exploited multiple vulnerabilities, including some that were only recently published, to inject OS command
Check Point Research encountered several attacks that exploited multiple vulnerabilities, including some that were only recently published, to inject OS command
 Now more than ever, we rely on our smartphones to keep in touch with our work, our families and the world around us. There are over 3.5 billion smartphone users
Now more than ever, we rely on our smartphones to keep in touch with our work, our families and the world around us. There are over 3.5 billion smartphone users
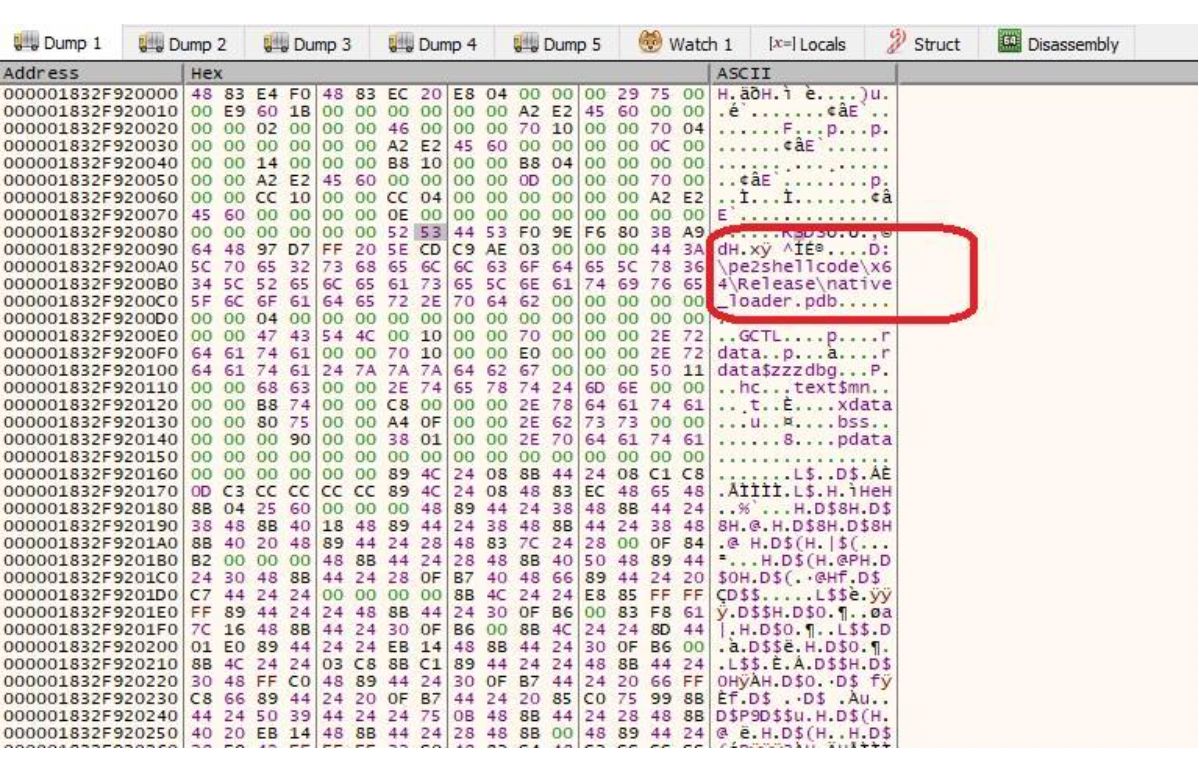
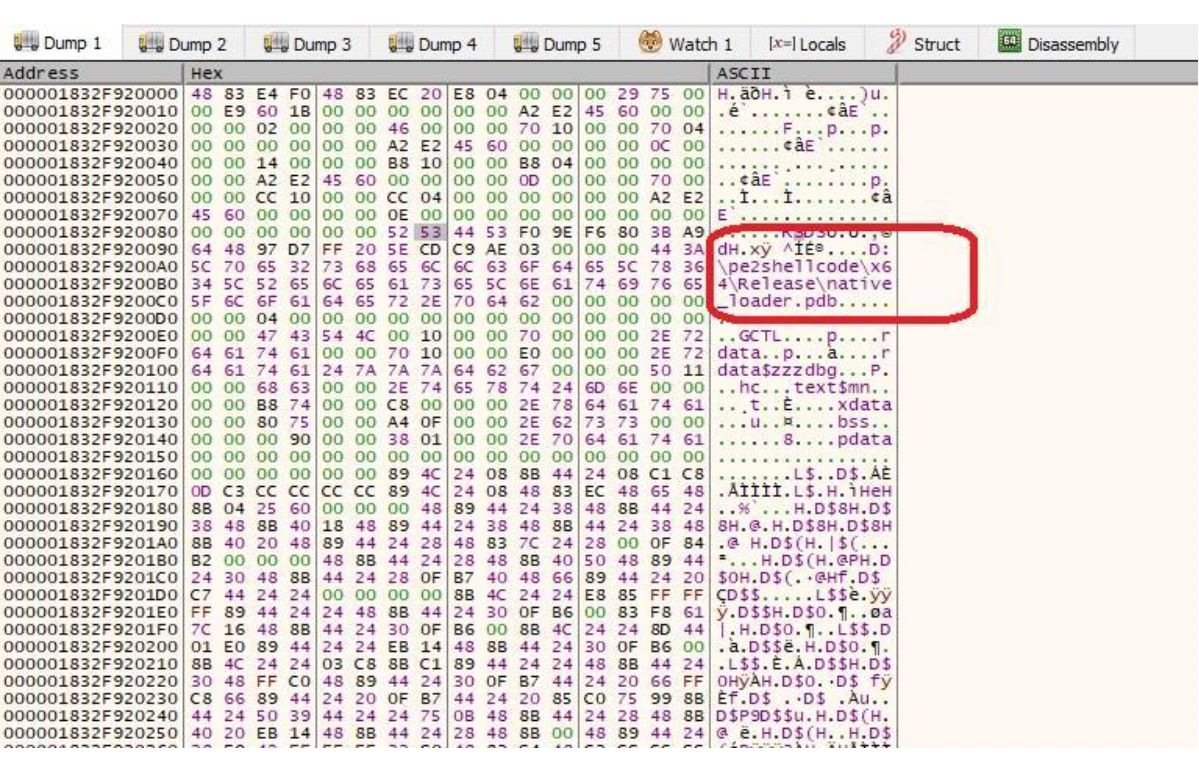
 When analyzing a complicated attack against one of our customers, we noticed a very small 64-bit executable that was executed by the malware.
When analyzing a complicated attack against one of our customers, we noticed a very small 64-bit executable that was executed by the malware.