Cybercrimes continue to be rampant and most people continue to wonder about their safety and that of their information.
Cybercrimes continue to be rampant and most people continue to wonder about their safety and that of their information.
 Nowadays, Cyber security is a trending topic around the globe. It has become a necessity for every business with the growing cyber threats.
Nowadays, Cyber security is a trending topic around the globe. It has become a necessity for every business with the growing cyber threats.
 Around mid-March, news filtered out of a cyberattack that hit the U.S. Health and Human Services (HHS) Department. Amid battling a pandemic, the HHS cyberinfrastructure was overloaded, but the HHS Secretary Alex Azar claimed that "we had no penetration into our networks, we had no degradation of the functioning of our networks."
Around mid-March, news filtered out of a cyberattack that hit the U.S. Health and Human Services (HHS) Department. Amid battling a pandemic, the HHS cyberinfrastructure was overloaded, but the HHS Secretary Alex Azar claimed that "we had no penetration into our networks, we had no degradation of the functioning of our networks."
 A recent Threatpost poll found that 40 percent of the companies transitioning to WFH experienced a spike in cyberattacks. The survey concluded that patching and updating are among the top challenges for employees when securing their remote footprint.
A recent Threatpost poll found that 40 percent of the companies transitioning to WFH experienced a spike in cyberattacks. The survey concluded that patching and updating are among the top challenges for employees when securing their remote footprint.
 Cyberattacks are growing day by day and causing a huge impact on the global economy.
Cyberattacks are growing day by day and causing a huge impact on the global economy.
 Cybercrime is on the rise when it comes to finding a target, online, dangers are diverse and they don't discriminate between companies and people.
Cybercrime is on the rise when it comes to finding a target, online, dangers are diverse and they don't discriminate between companies and people.
 Everybody in the IT industry should be aware of software security basics. It doesn’t matter if you’re a developer, system engineer, or product manager; security is everyone’s responsibility. Here’s a guide to essential software security terms.
Everybody in the IT industry should be aware of software security basics. It doesn’t matter if you’re a developer, system engineer, or product manager; security is everyone’s responsibility. Here’s a guide to essential software security terms.
 Enterprise administrators and individuals must defend their computer resources from numerous attacks to avoid a data breach
Enterprise administrators and individuals must defend their computer resources from numerous attacks to avoid a data breach
 The future belongs to information technologies that simultaneously provide proactive protection, backup, and data authenticity.
The future belongs to information technologies that simultaneously provide proactive protection, backup, and data authenticity.
 Attackers initiated a phishing campaign with emails that masqueraded as Xerox scan notifications, prompting users to open a malicious HTML attachment.
Attackers initiated a phishing campaign with emails that masqueraded as Xerox scan notifications, prompting users to open a malicious HTML attachment.
 One thing that has dogged the blockchain industry, more than most, is cyber-attacks.
One thing that has dogged the blockchain industry, more than most, is cyber-attacks.
 Man-in-the-middle attacks intercept communications for hackers to decrypt, letting them gain access to otherwise private information, bypassing security.
Man-in-the-middle attacks intercept communications for hackers to decrypt, letting them gain access to otherwise private information, bypassing security.
 Quantum technologies are steadily entering our life, and soon we will hear about new hacks using a quantum computer. So, how to protect against quantum attacks?
Quantum technologies are steadily entering our life, and soon we will hear about new hacks using a quantum computer. So, how to protect against quantum attacks?
 A study by the Wall Street Journal found that almost 70% of companies admitted concern about violent employees! While workers continue to be a major security ri
A study by the Wall Street Journal found that almost 70% of companies admitted concern about violent employees! While workers continue to be a major security ri
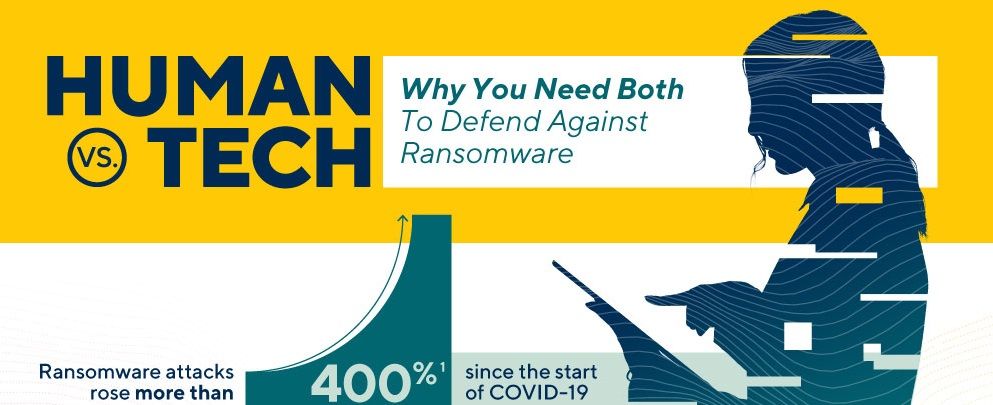
 It's going to take a mix of tech tools and human talent to prevent the ever increasing ransomware threats of the future.
It's going to take a mix of tech tools and human talent to prevent the ever increasing ransomware threats of the future.
 Cyber threats aimed at business are identified by Threat Intelligence.IT specialists and complex tools can read and analyze the threats
Cyber threats aimed at business are identified by Threat Intelligence.IT specialists and complex tools can read and analyze the threats
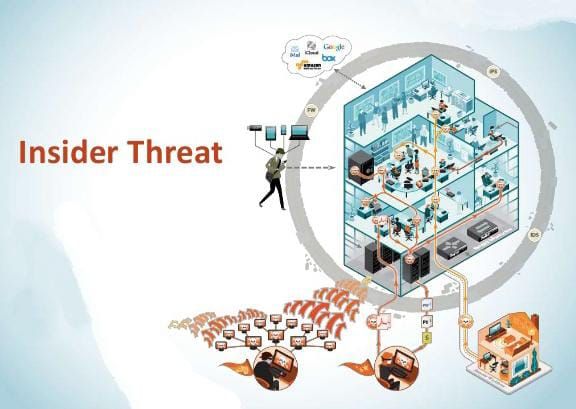
 In many cases, the person in a victim role may not be of any interest to criminals by him/herself, but the person or organization the victim is associated with.
In many cases, the person in a victim role may not be of any interest to criminals by him/herself, but the person or organization the victim is associated with.
 The Colonial Pipeline Breach has shown us that ransomware attacks are not going away anytime soon and having been increasing due to the COVID-19 pandemic.
The Colonial Pipeline Breach has shown us that ransomware attacks are not going away anytime soon and having been increasing due to the COVID-19 pandemic.
 On Tuesday, 20th April 2021, Biden’s administration issued a 100-day plan through the United States’s Power of energy to beep up cybersecurity.
On Tuesday, 20th April 2021, Biden’s administration issued a 100-day plan through the United States’s Power of energy to beep up cybersecurity.
 Sleep Tight - It Ain’t Gonna Be A Nuclear Fight!
Sleep Tight - It Ain’t Gonna Be A Nuclear Fight!
 In this article, we’re going to cover 7 of the best security sites on the internet.
In this article, we’re going to cover 7 of the best security sites on the internet.
 Scripps Health’s computer systems faced a ransomware attack this weekend and systems continue to plague the healthcare systems in San Diego.
Scripps Health’s computer systems faced a ransomware attack this weekend and systems continue to plague the healthcare systems in San Diego.
 A dusting attack involves sprinkling crypto wallets with minuscule amounts of crypto to connect multiple addresses to a single owner. While these attacks are relatively new and nobody has really been able to say for sure what the exact motives behind them are, what is clear is that they represent a significant threat to privacy on the blockchain.
A dusting attack involves sprinkling crypto wallets with minuscule amounts of crypto to connect multiple addresses to a single owner. While these attacks are relatively new and nobody has really been able to say for sure what the exact motives behind them are, what is clear is that they represent a significant threat to privacy on the blockchain.
 It is important to keep your data safe and secure. Here are six challenges in that hosting your data on the cloud can pose and how your data security can help.
It is important to keep your data safe and secure. Here are six challenges in that hosting your data on the cloud can pose and how your data security can help.
 With increased hacking activity focused on vulnerable businesses and at-home employees, cybersecurity has become a major business priority.
With increased hacking activity focused on vulnerable businesses and at-home employees, cybersecurity has become a major business priority.
 Pulse VPN exploitation chained with other vulnerabilities during an ongoing Red Team Operation to hack the company remotely. By Dhanesh Dodia - HeyDanny
Pulse VPN exploitation chained with other vulnerabilities during an ongoing Red Team Operation to hack the company remotely. By Dhanesh Dodia - HeyDanny
 Get to grips with the principle of planning, which is critical to any advanced operation, especially in the case of a serious cyber conflict
Get to grips with the principle of planning, which is critical to any advanced operation, especially in the case of a serious cyber conflict
 Mobile banking Trojans are now a common issue. With this malware, hackers steal money from smartphones. Keep your smartphone safe with these tips.
Mobile banking Trojans are now a common issue. With this malware, hackers steal money from smartphones. Keep your smartphone safe with these tips.
 Today I will tell you about various types of hacking techniques, and out of these, I will focus more on password hacking. There is no fixed classification of hacking, but I will tell you all the techniques that I remember. It is not possible to tell completely about all Hacking Techniques, so I will give you all the basic knowledge.
Today I will tell you about various types of hacking techniques, and out of these, I will focus more on password hacking. There is no fixed classification of hacking, but I will tell you all the techniques that I remember. It is not possible to tell completely about all Hacking Techniques, so I will give you all the basic knowledge.
 A look at the looming threat of cyberwar in the world stage of the Russia / Ukraine conflict
A look at the looming threat of cyberwar in the world stage of the Russia / Ukraine conflict
 Check Point Software’s Incident Response Team's guide for enterprises on how to prevent and deal with ransomware attacks.
Check Point Software’s Incident Response Team's guide for enterprises on how to prevent and deal with ransomware attacks.
 Tor and The Guardian (of the Journalistic Galaxy) also took their relationship to the next level.
Tor and The Guardian (of the Journalistic Galaxy) also took their relationship to the next level.
 Smart vehicles make driving a thrill! However, they are vulnerable to cyberattacks. Making smart security choices keeps you safe and your connected ride secure.
Smart vehicles make driving a thrill! However, they are vulnerable to cyberattacks. Making smart security choices keeps you safe and your connected ride secure.
 The face of modern cybercrime is not the stereotype of a hacker. It's a mirror, reflecting the people close to you. And the perpetrator could be anyone.
The face of modern cybercrime is not the stereotype of a hacker. It's a mirror, reflecting the people close to you. And the perpetrator could be anyone.
 It’s no secret that we’re living in uncertain times. Many countries are under partial or full lockdown for the past few weeks, making work from home the new norm for the foreseeable future, at least.
It’s no secret that we’re living in uncertain times. Many countries are under partial or full lockdown for the past few weeks, making work from home the new norm for the foreseeable future, at least.
 In this article of mine, I am going to discuss the best ways you can hack any wifi networks and what to do after hacking wifi, and how you can prevent it.
In this article of mine, I am going to discuss the best ways you can hack any wifi networks and what to do after hacking wifi, and how you can prevent it.
 On June 19 this year Australian Prime Minister, Scott Morrison, alerted the nation to the fact they were undergoing cyber attack.
On June 19 this year Australian Prime Minister, Scott Morrison, alerted the nation to the fact they were undergoing cyber attack.
 Remote work and how it has driven long-overdue reconsiderations of our connectivity, collaboration, and cybersecurity standards and approaches.
Remote work and how it has driven long-overdue reconsiderations of our connectivity, collaboration, and cybersecurity standards and approaches.
 The cyber-world now accommodates billions of users. There are more than 4 billion internet users in the world today. It's just unfortunate that a large percentage of these users face cyber attacks from unknown sources. While some users are afraid of being attacked, others are ignorant of possible attacks. As an organisation or an individual that utilises the internet, it's a must to know some security tricks. If you're wondering what the tricks are, read on.
The cyber-world now accommodates billions of users. There are more than 4 billion internet users in the world today. It's just unfortunate that a large percentage of these users face cyber attacks from unknown sources. While some users are afraid of being attacked, others are ignorant of possible attacks. As an organisation or an individual that utilises the internet, it's a must to know some security tricks. If you're wondering what the tricks are, read on.
 Due to the decentralized nature of the web3, cybersecurity becomes a major concern when protecting your non-custodial wallet on decentralized exchanges.
Due to the decentralized nature of the web3, cybersecurity becomes a major concern when protecting your non-custodial wallet on decentralized exchanges.
 Is always good not to share Your blockchain address and Your NFT IDs
Is always good not to share Your blockchain address and Your NFT IDs
 No business in the world can do away with cybercriminals. What’s worse, at times businesses are hit so hard, that they’re left with no other choice but to succumb to their losses.
No business in the world can do away with cybercriminals. What’s worse, at times businesses are hit so hard, that they’re left with no other choice but to succumb to their losses.
 82% of business leaders plan to continue letting employees work from home
82% of business leaders plan to continue letting employees work from home
 Check Point’s recent analysis of underground hacking communities revealed that cybercriminals are already utilizing AI-based tools for malicious purposes.
Check Point’s recent analysis of underground hacking communities revealed that cybercriminals are already utilizing AI-based tools for malicious purposes.
 A tech story centered around the looming issues of cybersecurity, cyber attacks, and the possible solutions in today's remote working ecosystem.
A tech story centered around the looming issues of cybersecurity, cyber attacks, and the possible solutions in today's remote working ecosystem.
 The Uyghurs, an ethnic minority in China have been targeted by fake human rights documents and websites intended to take advantage of their persecution in China
The Uyghurs, an ethnic minority in China have been targeted by fake human rights documents and websites intended to take advantage of their persecution in China
 This new wave of business digitalization increased the number of cyber attacks - the so-called cyber pandemic began.
This new wave of business digitalization increased the number of cyber attacks - the so-called cyber pandemic began.
 The attack was successful because two validators' private keys were suspected to be compromised.
The attack was successful because two validators' private keys were suspected to be compromised.
 Disagreement is one of the defining trends of 2020. However, I think most of us would agree that this year hasn’t turned out to be the kind of year that many of us anticipated when we celebrated on December 31st.
Disagreement is one of the defining trends of 2020. However, I think most of us would agree that this year hasn’t turned out to be the kind of year that many of us anticipated when we celebrated on December 31st.

 Blockchains aren't untouchable; they can and have been attacked in the past. Some blockchain attacks include a 51% attack and a 34% attack.
Blockchains aren't untouchable; they can and have been attacked in the past. Some blockchain attacks include a 51% attack and a 34% attack.
 If you don’t know, a bug bounty program is a modern strategy to encourage the public to find and report bugs or vulnerabilities in software — especially the security bugs that may be misused by cybercriminals. Most of the big technology companies like Facebook, Google, and Microsoft employ bug bounties.
If you don’t know, a bug bounty program is a modern strategy to encourage the public to find and report bugs or vulnerabilities in software — especially the security bugs that may be misused by cybercriminals. Most of the big technology companies like Facebook, Google, and Microsoft employ bug bounties.
 Public school systems often have limited budgets for cybersecurity safeguards and have become targets of more attacks.Amid a growing reliance on technology due to the coronavirus pandemic, cyberattacks have become a growing threat to schools across the United States – leading to school shutdowns and to demands for more funding to address the problem.
Public school systems often have limited budgets for cybersecurity safeguards and have become targets of more attacks.Amid a growing reliance on technology due to the coronavirus pandemic, cyberattacks have become a growing threat to schools across the United States – leading to school shutdowns and to demands for more funding to address the problem.
 Small businesses are the target of an avalanche of cyberattacks. To stop the insanity, here are some low-effort ways they can lower their risk.
Small businesses are the target of an avalanche of cyberattacks. To stop the insanity, here are some low-effort ways they can lower their risk.
 In this article, we’re going to take a look at some of the most common ways that companies get hacked as well as some of the most famous examples.
In this article, we’re going to take a look at some of the most common ways that companies get hacked as well as some of the most famous examples.
 These unprecedented times have pushed us to adapt distinctive lifestyles contrary to what we’ve been used to for a millenia. Industries like finance, law, banking and the public sector where culture has traditionally frowned upon working-from-home, are compelled to succumb to such mandates out of necessity. As much rampant the unfortunate layoffs, hiring freezes, and budget cuts across travel and hospitality industries are, data breaches have been on a steady rise. And this is an important observation that we can’t afford to overlook.
These unprecedented times have pushed us to adapt distinctive lifestyles contrary to what we’ve been used to for a millenia. Industries like finance, law, banking and the public sector where culture has traditionally frowned upon working-from-home, are compelled to succumb to such mandates out of necessity. As much rampant the unfortunate layoffs, hiring freezes, and budget cuts across travel and hospitality industries are, data breaches have been on a steady rise. And this is an important observation that we can’t afford to overlook.
 Over the years, social engineering assaults have been a regular phenomenon against companies. It has become more and more sophisticated.
Over the years, social engineering assaults have been a regular phenomenon against companies. It has become more and more sophisticated.
 Zero-Day Attacks are becoming increasingly common and widespread in the world of cybersecurity. Heuristics detection may help to detect such vulnerabilities.
Zero-Day Attacks are becoming increasingly common and widespread in the world of cybersecurity. Heuristics detection may help to detect such vulnerabilities.
 Instances of cyberattacks, especially those targeting WordPress websites, are on the rise across the internet. The most recent attack to hit WordPress users affected some 700,000 sites running a vulnerable plugin.
Instances of cyberattacks, especially those targeting WordPress websites, are on the rise across the internet. The most recent attack to hit WordPress users affected some 700,000 sites running a vulnerable plugin.
 White hat hackers find and exploit vulnerabilities within a company's network or system with the intention to provide remediation steps to mitigate these risks.
White hat hackers find and exploit vulnerabilities within a company's network or system with the intention to provide remediation steps to mitigate these risks.
 The Badger DAO attack was conceptually very different from the more traditional attack in DeFi. Those traditional ones are aimed at exploiting vulnerabilities in the code of smart contracts of the protocols, otherwise called bugs. We are familiar with flash loan attacks that use uncollateralised loans across a multitude of protocols to manipulate certain markets and pump-and-dump certain assets. We also know about reentrancy attacks that exploit the logic of execution of functions inside a smart contract. However, the Badger DAO exploit was both more and less ingenious at once.
The Badger DAO attack was conceptually very different from the more traditional attack in DeFi. Those traditional ones are aimed at exploiting vulnerabilities in the code of smart contracts of the protocols, otherwise called bugs. We are familiar with flash loan attacks that use uncollateralised loans across a multitude of protocols to manipulate certain markets and pump-and-dump certain assets. We also know about reentrancy attacks that exploit the logic of execution of functions inside a smart contract. However, the Badger DAO exploit was both more and less ingenious at once.
 Taking a look at the 5 most common types of cybercrime in 2022 and how to defend yourself
Taking a look at the 5 most common types of cybercrime in 2022 and how to defend yourself
 According to Naval Dome, the maritime industry has seen a 900% increase in cyber-attacks since 2017
According to Naval Dome, the maritime industry has seen a 900% increase in cyber-attacks since 2017
 Verizon’s 2020 Data Breach Investigations Report shows that 80% of the breaches caused by hacking involve brute-force or the use of lost or stolen credentials. The content management systems (CMS) are the usual targets of brute-force attacks, as 39.3% of all the websites presumably run on WordPress, the most popular of these.
Verizon’s 2020 Data Breach Investigations Report shows that 80% of the breaches caused by hacking involve brute-force or the use of lost or stolen credentials. The content management systems (CMS) are the usual targets of brute-force attacks, as 39.3% of all the websites presumably run on WordPress, the most popular of these.
 SIM swap fraud prevention is something everyone should know about to fight identity theft. This article will define SIM swapping and how to prevent it.
SIM swap fraud prevention is something everyone should know about to fight identity theft. This article will define SIM swapping and how to prevent it.
 Hermit Spyware is an advanced spyware designed to target iOS and Android mobile devices.
Hermit Spyware is an advanced spyware designed to target iOS and Android mobile devices.
 If there's one thing that there's no shortage of, it's small businesses. In the US alone, there are over thirty million of them. And by and large, they're doing a miserable job of protecting themselves against a rising wave of cyber-attacks and digital risk.
If there's one thing that there's no shortage of, it's small businesses. In the US alone, there are over thirty million of them. And by and large, they're doing a miserable job of protecting themselves against a rising wave of cyber-attacks and digital risk.
 Following the successful but expensive launch and sales of digital land plots of Yuga Labs’ metaverse, Ava Labs submitted a proposal suggesting that Avalanche is the ideal blockchain ecosystem for the highly anticipated Otherside metaverse.
Following the successful but expensive launch and sales of digital land plots of Yuga Labs’ metaverse, Ava Labs submitted a proposal suggesting that Avalanche is the ideal blockchain ecosystem for the highly anticipated Otherside metaverse.
 Automation can stand as a mighty knight for the fortress of your organization by strengthening cybersecurity. Collect data and speed up response time.
Automation can stand as a mighty knight for the fortress of your organization by strengthening cybersecurity. Collect data and speed up response time.
 During the stressful COVID-19 pandemic, governments are urging people to stay home. So, many people have adopted new ways to run their day-to-day lives and make sure they are fulfilling. Zoom keeps millions of people connected. TikTok provides a creative outlet to escape shelter-in-place boredom. And Amazon is selling everything from N95 masks to those special I-need-this-in-my-life items.
During the stressful COVID-19 pandemic, governments are urging people to stay home. So, many people have adopted new ways to run their day-to-day lives and make sure they are fulfilling. Zoom keeps millions of people connected. TikTok provides a creative outlet to escape shelter-in-place boredom. And Amazon is selling everything from N95 masks to those special I-need-this-in-my-life items.
 24 February 2022 - the day Russian Federation started open military aggression against Ukraine and changed the global cybersecurity landscape.
24 February 2022 - the day Russian Federation started open military aggression against Ukraine and changed the global cybersecurity landscape.
 I believe strongly if we get answers to these questions from a source with gravitas, such as Sabu, we will understand how to navigate the future.
I believe strongly if we get answers to these questions from a source with gravitas, such as Sabu, we will understand how to navigate the future.
 Software supply chain attacks can take many forms, but the most common method is through the insertion of malicious code into the software development process.
Software supply chain attacks can take many forms, but the most common method is through the insertion of malicious code into the software development process.
 As Chief Technologist for Avant Research Group in Buffalo, New York, and formerly as a professor at the University of Buffalo, Arun Vishnawath has spent his professional and academic career studying the “people problem” of cybersecurity.
As Chief Technologist for Avant Research Group in Buffalo, New York, and formerly as a professor at the University of Buffalo, Arun Vishnawath has spent his professional and academic career studying the “people problem” of cybersecurity.
His current research focuses on improving individual, organizational, and national resilience to cyber attacks by focusing on the weakest links in cybersecurity — Internet users.
 Ransomware is a different kind of malware. Find out how to identify and prevent its attacks that encrypt your files and demand a paid ransome for data access.
Ransomware is a different kind of malware. Find out how to identify and prevent its attacks that encrypt your files and demand a paid ransome for data access.
 The US government proclaimed a regional emergency, as the largest fuel pipeline system remained shut down for two days due to ransomware.
The US government proclaimed a regional emergency, as the largest fuel pipeline system remained shut down for two days due to ransomware.
 In this thread, our community discusses their thoughts on the latest scams, including the LinkedIn Bogus Boss scam on the rise.
In this thread, our community discusses their thoughts on the latest scams, including the LinkedIn Bogus Boss scam on the rise.
 More than 1,700 security breaches were reported in the first six months of 2021. This begs the question, are we actually safe on the internet?
More than 1,700 security breaches were reported in the first six months of 2021. This begs the question, are we actually safe on the internet?
 Recently MITRE Engenuity announced significant innovations helping cybersecurity professionals to work under the same language.
Recently MITRE Engenuity announced significant innovations helping cybersecurity professionals to work under the same language.
 Check Point Research encountered several attacks that exploited multiple vulnerabilities, including some that were only recently published, to inject OS command
Check Point Research encountered several attacks that exploited multiple vulnerabilities, including some that were only recently published, to inject OS command
 Over the years, the number of devices connected to the Internet has increased exponentially. From a little over 15 billion devices in 2015, over 26.6 billion devices were connected in 2019.
Over the years, the number of devices connected to the Internet has increased exponentially. From a little over 15 billion devices in 2015, over 26.6 billion devices were connected in 2019.
 Why the SUNBURST incident is more alarming than the FireEye’s hack.
Why the SUNBURST incident is more alarming than the FireEye’s hack.
 The Biden administration is coming up with a $100 billion investment plan fo cybersecurity spending.
The Biden administration is coming up with a $100 billion investment plan fo cybersecurity spending.
 A zero-day exploit can endanger a person’s life if the devices are not secured with the potential cyber threats in mind. Here are tips to secure healthcare tech
A zero-day exploit can endanger a person’s life if the devices are not secured with the potential cyber threats in mind. Here are tips to secure healthcare tech
 Recently, Check Point Research encountered a series of worldwide attacks relevant to VoIP, specifically to Session initiation Protocol (SIP) servers
Recently, Check Point Research encountered a series of worldwide attacks relevant to VoIP, specifically to Session initiation Protocol (SIP) servers