Replies: 1 comment
-
|
@kraison1 this is an incredibly complex issue. Whether or not the CVE should be considered applicable depends ultimately on whether or not there are any code paths which pass untrusted user input into Simply having ejs in your dependency graph does not automatically mean this CVE can be exploited in your application, but security tools which only look at your SBOM don't have this kind of context, so they err on the side of caution, and it's up to you to be able to rule it in or out (and also up to your organisation to have adequate processes for marking these findings as false positives). The fact that ejs is a transitive dependency nested 4 levels deep from react-scripts (you've missed one in your dependency path... it's actually react-scripts -> workbox-webpack-config -> workbox-build -> rollup-plugin-off-main-thread -> ejs) means there are a lot of ways
If your app is using any other dependencies which make any of the above calls, then you need to check the code paths there, to see if they are passing untrusted input. Based on my reading of the code, react-scripts does not appear to have any direct references to Unless, of course, I've missed something here. |
Beta Was this translation helpful? Give feedback.
Uh oh!
There was an error while loading. Please reload this page.
Uh oh!
There was an error while loading. Please reload this page.
-
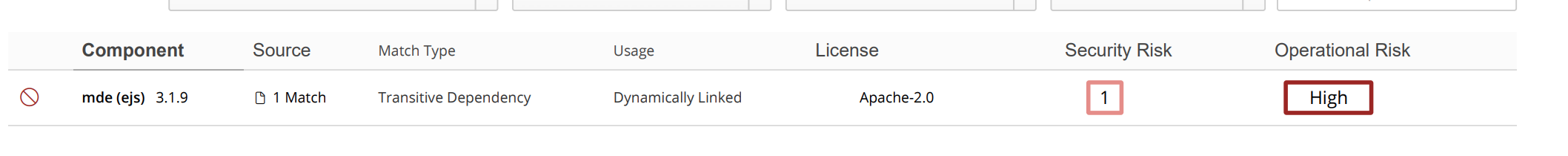
Ref nvd: https://nvd.nist.gov/vuln/detail/CVE-2023-29827
Dependency Path: react-scripts (5.0.1) -> workbox-build (6.6.0) -> @surma/rollup-plugin-off-main-thread (2.2.3) -> ejs(3.1.9)

Img nvd
Img black duck
Beta Was this translation helpful? Give feedback.
All reactions